5 reasons to move to a network platform
CIO
FEBRUARY 27, 2024
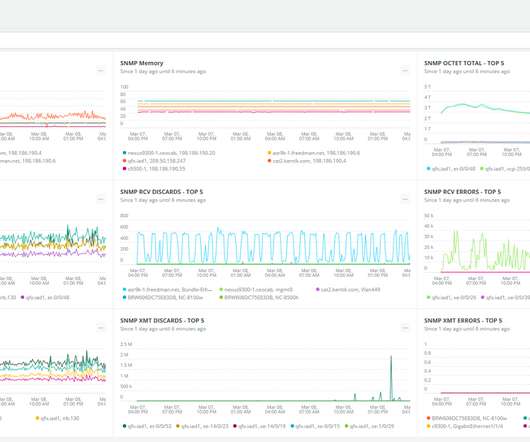
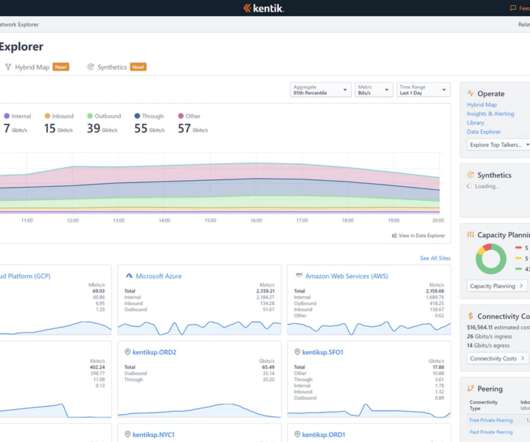
AI helps automate remediation when issues like wireless interference and WAN bottlenecks are uncovered and can also be applied to help predict and prevent network degradation from occurring in the first place. AI can help create better-informed insights while constructing an end-to-end view of service delivery and performance.

















































Let's personalize your content