The Common Drawbacks of Selecting ERP Software for Small Business
OTS Solutions
APRIL 2, 2020
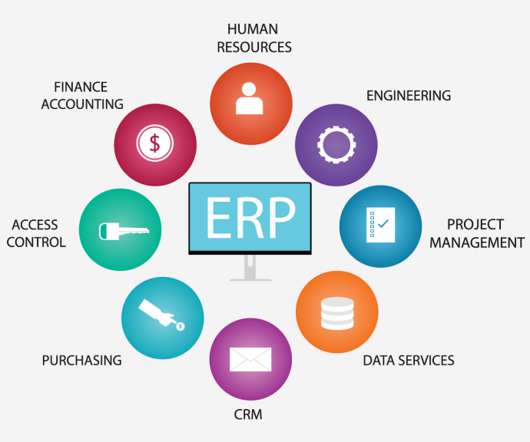
Despite the technicalities of running a business, running a business can be boiled down to efficiently managing business processes. Business processes are looked at as the building blocks of a business which include sales and marketing, customer services, and virtually everything else in between. Managing all of these processes not only requires time, but it also requires a good chunk of manpower that may take away from other areas of a business.





































Let's personalize your content