Radically simplify and expand Zero Trust to cloud workload
CIO
DECEMBER 21, 2023
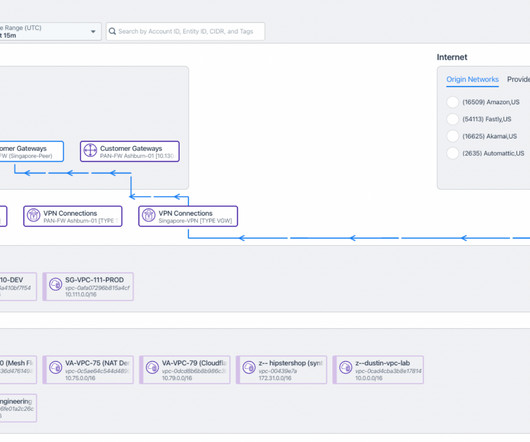
Many organizations rely on legacy security architectures to secure their cloud workloads. They often use a combination of: Cloud native security solutions offered by cloud service providers Multiple security tools (firewall, VPN, TLS/SSL inspection, DLP, etc.)




















































Let's personalize your content