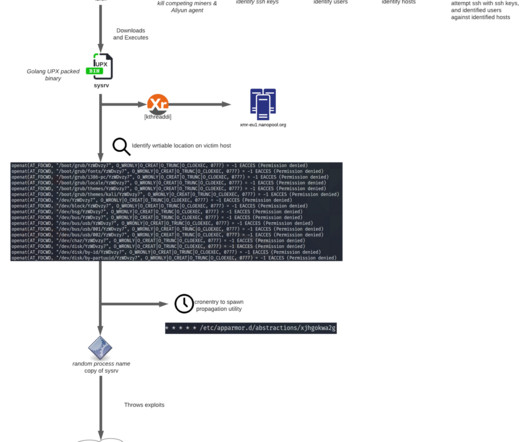
Resolving Embedded Files at Runtime via strace
Lacework
FEBRUARY 27, 2023
Jared Stroud Cloud Security Researcher, Lacework Labs Modern Linux malware binaries are being shipped with one or more embedded files. Prior to the “real payload” being dropped, it’s common to see checks for the host’s CPU architecture, Linux distribution or […]















































Let's personalize your content