Setup keyless authentication to Google Cloud for GitHub Actions using Terraform
Xebia
JANUARY 18, 2023
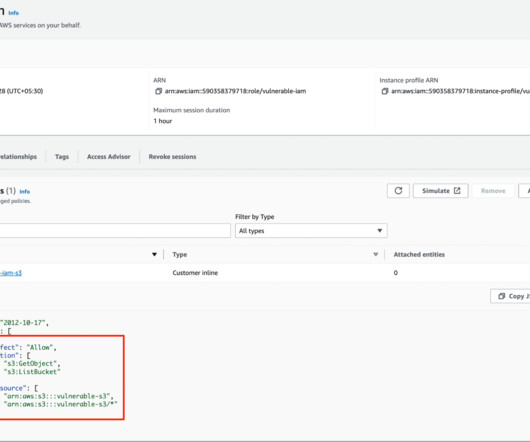
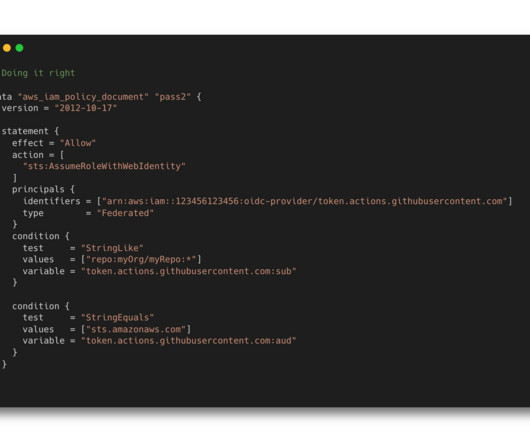
When a GitHub Actions workflow needs to read or mutate resources on Google Cloud it must first authenticate to the platform. Not only does this cause a security risk for leaking this key, but it might also be that the creation of this key is blocked by your organization’s policy.

















































Let's personalize your content