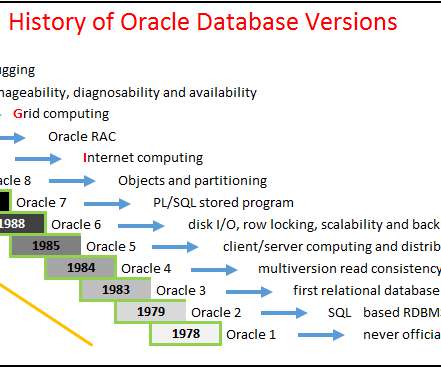
Let’s Compare: BARMAN vs. Manual Backup
Datavail
MAY 6, 2020
BARMAN is one of the most popular tools for backup and recovery management in PostgreSQL. PostgreSQL, as an open source database has different methods to approach database backups. Manual Backup Methods. Pg_dump (Logical Backup). Logical backups can be table level to database level based on requirements.

















































Let's personalize your content