Four Priorities for Better Endpoint Management in 2020
Kaseya
JANUARY 23, 2020
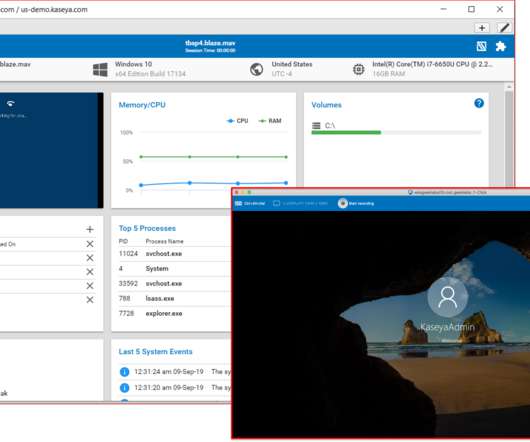
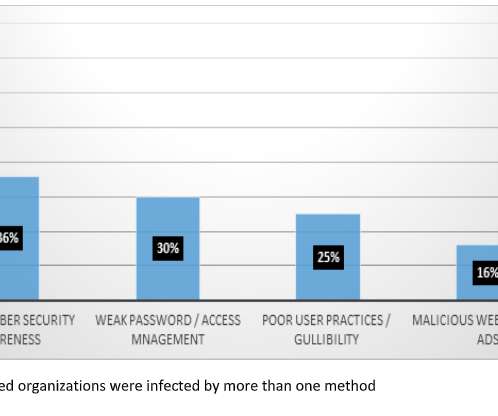
The report identifies their top priorities for effective endpoint management and helps in selecting the right solution according to business needs. Kaseya was selected as a Top 3 vendor in two of the categories in the report– Patch Management and Asset and Inventory Management. Endpoint Backup and Recovery .








































Let's personalize your content