How AI-Powered Security Capabilities Implement Real-Time Cybersecurity
Palo Alto Networks
JANUARY 18, 2024
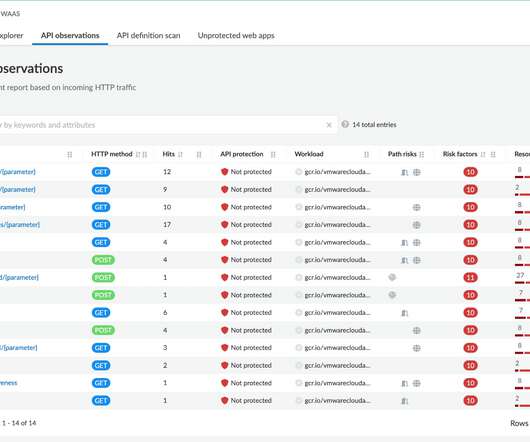
Moreover, the use of AI to address these challenges is critical to allow your organization to utilize real-time data and intelligence for timely threat detection and incident response, overcoming data and operational silos (e.g., across network infrastructure, cloud assets, endpoints, industrial OT environments etc.).



















































Let's personalize your content