TDD saved the day
Xebia
JUNE 6, 2023
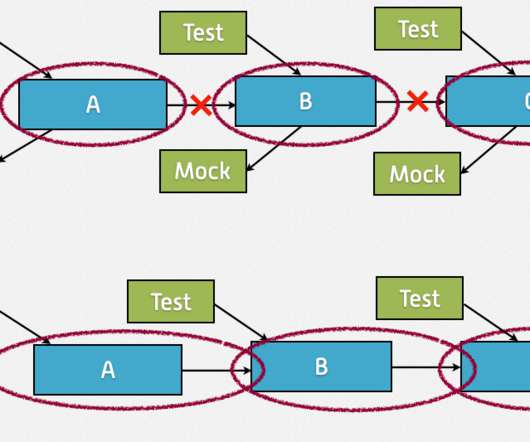
Armed with a few assumptions about how things should work, I embarked on developing an application with a graphical UI and a backend. The goal was to compare two object graphs and present them in a way a user could selectively merge them. This was convenient as it allowed me to maintain a TDD flow without external dependencies.




















































Let's personalize your content