From Manifest to Workload: Embedding Kubernetes Security at Each Phase of the DevOps Lifecycle
Prisma Clud
JANUARY 24, 2023
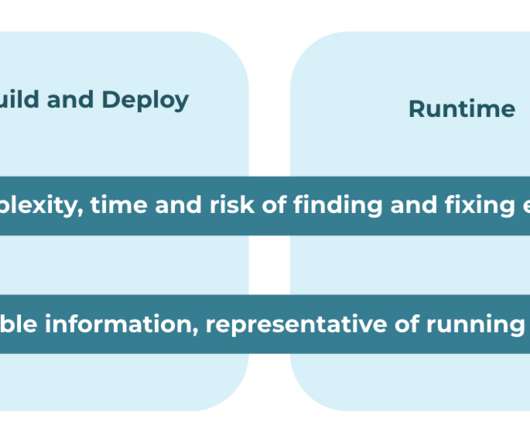
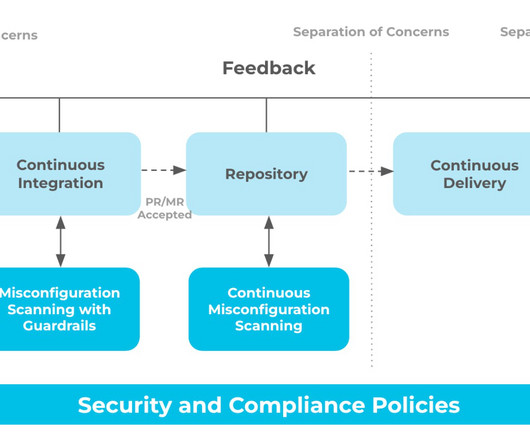
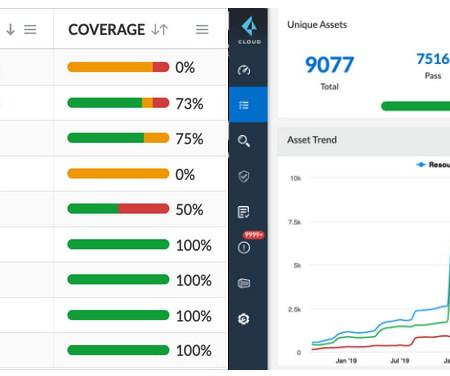
But the other part of the key to Kubernetes security—and the one that is easier to overlook—is the DevOps lifecycle. Kubernetes doesn’t exist in a vacuum; in most cases, it leverages infrastructure as code (IaC) and is part of a continuous integration/continuous delivery (CI/CD) pipeline that DevOps teams use to deliver software.
















































Let's personalize your content