5 Steps for Becoming a Business-Aligned Cybersecurity Leader
Tenable
SEPTEMBER 30, 2020
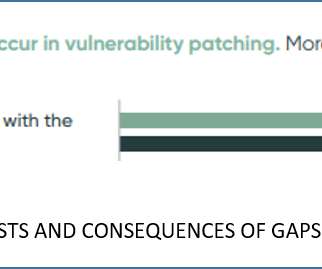
Independent business risk study shows when security and the business are aligned around agreed-upon contextual data, they deliver demonstrable results. Folks, cybersecurity is broken. Security leaders are drowning in data. Because we're missing one key piece of information: business context. Here's how to get there.






































Let's personalize your content