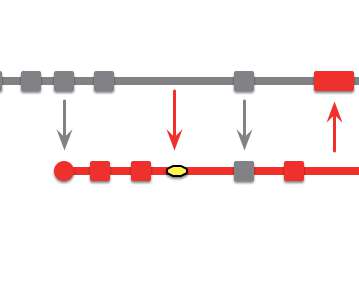
Branching Pattern: Healthy Branch
Martin Fowler
APRIL 22, 2020
On each commit, perform automated checks, usually building and running tests, to ensure there are no defects on the branch. more….
Martin Fowler
APRIL 22, 2020
On each commit, perform automated checks, usually building and running tests, to ensure there are no defects on the branch. more….

Arista
APRIL 22, 2020
Just a decade ago, public cloud titans Amazon Web Services and Microsoft Azure Cloud, became synonymous with elastic scaling, and software provisioning through APIs. This was a phenomenon that didn’t exist within closed legacy systems. Private clouds, by contrast, saw the relevance of enterprise customers recreating an infrastructure based on public cloud principles operating at a smaller scale.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.
The Crazy Programmer
APRIL 22, 2020
Many organizations find themselves looking for software solutions that simply do not exist on the market today. After endless searching, they finally decide to seek out a software development company, like BairesDev , to turn their ideas into a reality. The process of custom software development is the designing, creation, deployment, and maintenance of software built for a specific user, function, or organization as a whole.

Dataiku
APRIL 22, 2020
Here at Dataiku, we frequently stress the importance of collaboration in building a successful data team. In short, successful data science and analytics are just as much about creativity as they are about crunching numbers, and creativity flourishes in a collaborative environment.

Advertisement
Many organizations today are unlocking the power of their data by using graph databases to feed downstream analytics, enahance visualizations, and more. Yet, when different graph nodes represent the same entity, graphs get messy. Watch this essential video with Senzing CEO Jeff Jonas on how adding entity resolution to a graph database condenses network graphs to improve analytics and save your analysts time.

Netlify
APRIL 22, 2020
Gatsby recently released incremental builds , an improvement that reduces the amount of work required to build a Gatsby site. In this post, we’ll learn how to enable Gatsby incremental builds on Netlify. Step 1: Upgrade to Gatsby v2.20.4 or higher. Gatsby introduced incremental builds in version 2.20.4, so make sure to upgrade your Gatsby site to the latest version. # this will upgrade to the latest version of Gatsby npm install gatsby@latest.
CTO Universe brings together the best content for CTOs from the widest variety of industry thought leaders.

CTOvision
APRIL 22, 2020
We are tracking OPSWAT in our Guide to Technology as a Cybersecurity Company. OPSWAT is trusted by over 1,000 organizations worldwide to protect infrastructure and reduce risk from cyber attack. Their goal: Eliminate malware and zero-day attacks. They designed their solutions with an understanding that every file and every device could pose a threat, so […].

DevOps.com
APRIL 22, 2020
The COVID-19 global pandemic has ushered a significant priority shift for the digital workplace. As development teams become completely remote, executive priorities are rapidly adapting to meet the gravity of these unanticipated times. But, were IT leaders prepared for such a dramatic shift? What are they doing to evolve? To answer these tough questions, let’s […].

CTOvision
APRIL 22, 2020
Read why Brandon Vigliarolo says that the COVID-19 lockdowns have caused a spike in data breach incidents on the Tech Republic : The International Association of IT Asset Managers (IATAM) is warning that at-home work due to the COVID-19 pandemic is leading to a spike in data breaches that’s greater than anticipated. IATAM raised the […].

TechBeacon
APRIL 22, 2020
Before the COVID-19 pandemic, most organizations viewed working at home as a perk, a nice-to-have, bait to dangle before a prospective employee. Now, with many workers confined to their homes to avoid the spread of the coronavirus, it's become a necessity.

Advertisement
IT leaders know the importance of compliance at every level, but the database often gets left behind as other environments are automated for robust protection. This whitepaper emphasizes the importance of robust, auditable, and secure database change management practices for safeguarding organizational compliance. Learn how automating database compliance: Mitigates risk Protects against security vulnerabilities Helps avoid regulatory penalties Aligns database workflows with app lifecycle Turns d

CTOvision
APRIL 22, 2020
Read why Matt Middleton-Leal says that it is difficult to combat insider threats as more and more business communications are using cloud on Tech Radar : Cloud providers including Microsoft, Google, and others, have recently acknowledged that they are struggling to deal with a spike in remote tools usage. As organisations hastily adapt for remote working, […].

DevOps.com
APRIL 22, 2020
DevSecOps has become an increasingly popular topic as enterprises grapple with the continuing challenge of improving their cybersecurity infrastructure. As the first quarter of 2020 has come to a close, are we making significant progress in fully integrating the development, operations and security functions in the enterprise? The term “DevOps” was first used in 2009 […].

CTOvision
APRIL 22, 2020
Read David Gray explain how you can implement as optimum remote incident response plan during the COVID-19 pandemic on Infosec Magazine : Cybersecurity threats have risen by over 37% in the last month, with threat actors and cyber-criminals using the fear brought on by the COVID-19 pandemic as a target of opportunity to further their […].

N2Growth Blog
APRIL 22, 2020
COVID-19 has made CEO marketing priorities synonymous with survival. CEOs who have a focused, crisp, creative, and clear message, and who understand how to best communicate that message, will navigate the pandemic better than their less-skilled peers. The following are five tips to help CEOs refine and distribute their message during the coronavirus pandemic.

Speaker: Aarushi Kansal, AI Leader & Author and Tony Karrer, Founder & CTO at Aggregage
Software leaders who are building applications based on Large Language Models (LLMs) often find it a challenge to achieve reliability. It’s no surprise given the non-deterministic nature of LLMs. To effectively create reliable LLM-based (often with RAG) applications, extensive testing and evaluation processes are crucial. This often ends up involving meticulous adjustments to prompts.

CTOvision
APRIL 22, 2020
According to the latest Cloud Security Alliance (CSA) report on the 11 biggest threats to cloud computing, misconfiguration and inadequate change control ranked second only to — you guessed it — data breaches. The Capital One incident, in which data on 106 million credit card customers and applicants was exposed, is a good example. The attackers […].

Toptal
APRIL 22, 2020
Missing the luxury of a good, old-fashioned remote control when the laptop is beyond easy reach? Transform your old smartphone into a remote and learn some basic Node.js/Express/Pug along the way.
O'Reilly Media - Ideas
APRIL 22, 2020
Three months ago, Apple released a new credit card in partnership with Goldman Sachs that aimed to disrupt the highly regulated world of consumer finance. However, a well-known software developer tweeted that he was given 20x the credit line offered to his wife, despite the fact that they have been filing joint tax returns and live in a community property state.

Datavail
APRIL 22, 2020
Modernization of legacy technology isn’t just a good idea or the path to marketplace competitiveness. Instead, it’s rapidly becoming the only strategy available to ensure that most companies will be able to compete in the future. Not only are consumers expecting to interact with a fully functional, evolved digital system, but more regulators and watchdogs are requiring the upgrades, too.

Advertisement
Multi-tenant architecture allows software vendors to realize tremendous efficiencies by maintaining a single application stack instead of separate database instances while meeting data privacy needs. When you use a data warehouse to power your multi-tenant analytics, the proper approach is vital. Multi-tenant analytics is NOT the primary use case with traditional data warehouses, causing data security challenges.

Aqua Security
APRIL 22, 2020
Container images are a growing path for external code to enter an organization. Docker has simplified image workflow in order to encourage adoption by developers, so anyone can pull and run images that were built and pushed to Docker Hub, often by unknown individuals. This is being exploited by malicious actors to embed sophisticated malware in innocent-looking images.

CEO Insider
APRIL 22, 2020
There’s no doubt that businesses are being severely impacted by the COVID-19 pandemic. COVID-19 is a tiny, invisible virus that has created a large and visible change around the world. Seemingly overnight, and with little advance notice, our world and the business landscape changed. Business routines have been uprooted. But, with every wind of change […].

Tenable
APRIL 22, 2020
Microsoft responds to a recent security advisory from Autodesk by publishing an out-of-band advisory for Office products integrating the Autodesk library. Background. On April 15, Autodesk released a security advisory, ADSK-SA-2020-0002 , to address six vulnerabilities in the Autodesk Filmbox (FBX) Software Development Kit, which “allows application and content vendors to transfer existing content into the FBX format with minimal effort.”.
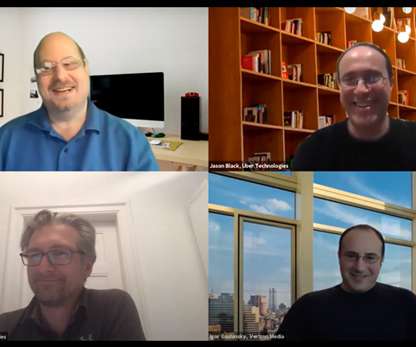
Kentik
APRIL 22, 2020
Last week Kentik hosted its second virtual panel on scaling networks and services during COVID-19. As our moderator, Kentik Co-founder and CEO Avi Freedman was joined by network leaders from Akamai, Uber and Verizon Media, namely: Christian Kaufmann, VP of Network Technology, Akamai. Jason “JB” Black, Head of Global Network Infrastructure, Uber. Igor Gashinsky, Chief Network Architect, VP, Verizon Media.

Advertisement
Apache Cassandra is an open-source distributed database that boasts an architecture that delivers high scalability, near 100% availability, and powerful read-and-write performance required for many data-heavy use cases. However, many developers and administrators who are new to this NoSQL database often encounter several challenges that can impact its performance.

DevOps.com
APRIL 22, 2020
The HashiCorp Cloud Engineering Certifications are designed to help technologists demonstrate their expertise with fundamental capabilities needed in today’s multi-cloud world. Organizations of all sizes have embraced cloud technology and are adopting a cloud operating model for their application workloads. This new model of computing is inherently multi-cloud and driven by a need for heterogeneous, on-demand, self-service […].

Github
APRIL 22, 2020
GitHub Actions puts powerful CI/CD and automation directly into the developer workflow, and it became generally available just six months ago. Since then, we’ve continued to improve with artifact and dependency caching for faster workflows, self-hosted runners for greater flexibility, and the Actions API for extensibility. The community response has been amazing and we’re excited to share some new and upcoming enhancements.

Teradata
APRIL 22, 2020
In light of COVID-19's massive disruption of our global economy and daily lives, it is more important than ever to enable fully digital and data-driven supply chains.

Dzone - DevOps
APRIL 22, 2020
Intro note: This piece was written before concerns over coronavirus changed the way dev orgs work. All of the tips in this blog are still 100% relevant, but if I wrote today I might have changed the title a bit. Tips for Translating Engineering to Executives. A lot has been said about how lonely it gets being a founder/CEO of a startup company; you can probably pick any Ben Horowitz quotes here about the struggle or the cold sweat in the middle of the night and you’d be right.

Advertisement
“Reimagined: Building Products with Generative AI” is an extensive guide for integrating generative AI into product strategy and careers featuring over 150 real-world examples, 30 case studies, and 20+ frameworks, and endorsed by over 20 leading AI and product executives, inventors, entrepreneurs, and researchers.

Palo Alto Networks
APRIL 22, 2020
As threat actor techniques continue to get more targeted and sophisticated, there is more pressure than ever on detection and response vendors to continually test and improve detection methods. The MITRE ATT&CK evaluations were created to test the detection capabilities of leading endpoint security vendors by emulating the real-world attack sequences of sophisticated advanced persistent threat (APT) groups from around the world. .

IDC
APRIL 22, 2020
Explore the 5 elements that create a hierarchy of trust in organizations that will empower enterprises to deliver competitive advantage with IDC's Frank Dickson.

thoughtLEADERS, LLC
APRIL 22, 2020
Maureen Metcalf, thoughtLEADERS Principal, sat down with Jim and Jan of The Leadership Podcast to discuss her thoughts on resilient leadership. In continuation of our new collaboration with The Leadership Podcast, Maureen talks about developing and being a resilient leader in this short form “chalk talk.” These chalk talk series are bitesize sessions on a common (but challenging) leadership issue.
Let's personalize your content