Socket lands $4.6M to audit and catch malicious open source code
TechCrunch
MAY 11, 2022
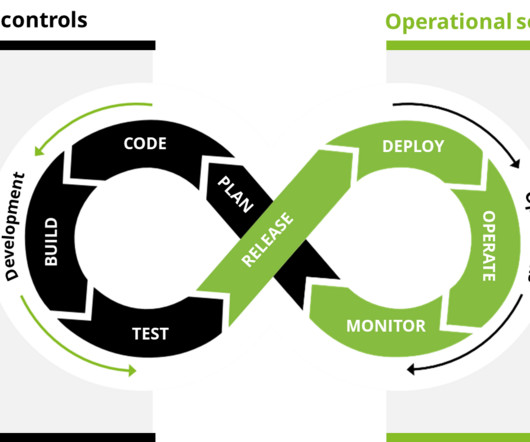
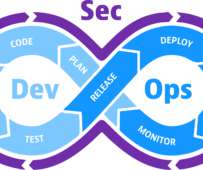
Securing the software supply chain is admittedly somewhat of a dry topic, but knowing which components and code go into your everyday devices and appliances is a critical part of the software development process that billions of people rely on every day.


















































Let's personalize your content