Due diligence is ever more critical as the battle for cloud sovereignty intensifies
CIO
DECEMBER 21, 2022
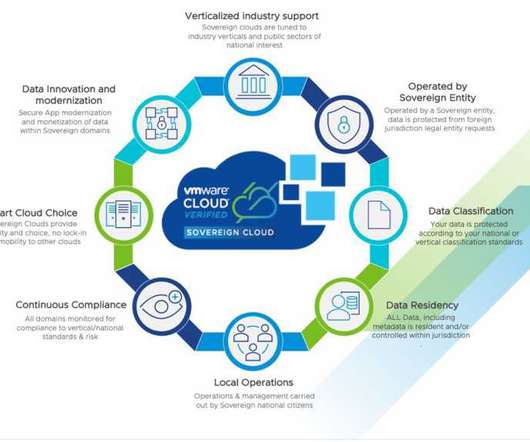
After Google’s cooperation with T-Systems and the “ Delos ” offer from Microsoft, SAP, and Arvato, AWS now follows suit. hyperscale organizations into expansion means that no European cloud company will ever seriously challenge this market today. CLOUD Act or Section 702 of the US Foreign Intelligence Surveillance Act (FISA).





















































Let's personalize your content