Best Practices for Managing Vulnerabilities in the Cloud–Part 1
Prisma Clud
MAY 2, 2024
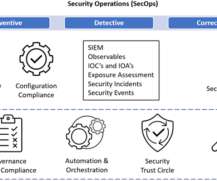
If you’ve ever questioned the importance of vulnerability management, consider these facts: 26,447 vulnerabilities were disclosed in 2023—1,500 more than in 2022. Three new vulnerabilities are discovered every 3 hours. Does your team have a plan to effectively manage vulnerabilities in the cloud?





















































Let's personalize your content