AWS ClientVPN SAML-based authentication via Tools4ever HelloID
Xebia
AUGUST 10, 2023
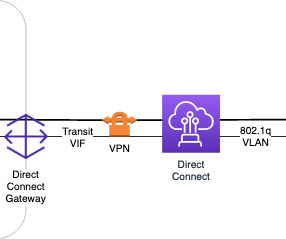
Extensive documentation exists for implementing SAML-based authentication for AWS Client VPN through IDPs like Okta and Azure AD, but if you or your customers happen to use a different IDP – documentation is hard to come by. Towards the end of this article we take a look at authorization rules as implemented by AWS Client VPN.
















































Let's personalize your content