The Importance of Security and Compliance in Enterprise Applications
OTS Solutions
JUNE 21, 2023
DDoS attacks are executed by a network of devices, often compromised computers and IoT (Internet of Things) devices that have been co-opted into a botnet. This may include implementing advanced firewalls, deploying DDoS mitigation technologies, and establishing an incident response plan.













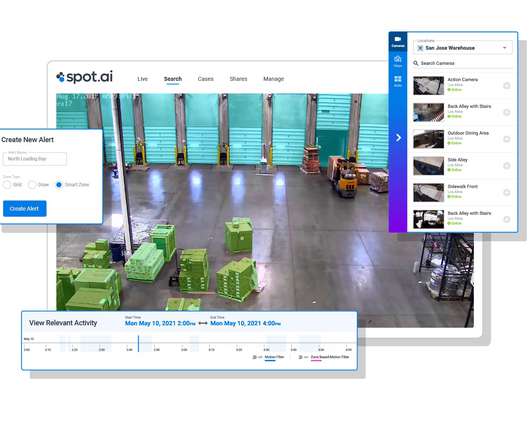
























Let's personalize your content