Securing Microservices Vs. Monolithic Apps
DevOps.com
AUGUST 10, 2021
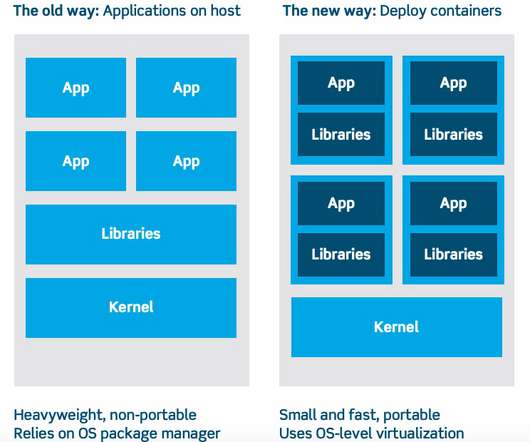
New requirements for Securing Microservices Vs. Monolithic Apps Enterprises are migrating from monolithic applications to microservices, hoping to accelerate software deployment and improve scalability. Security is sometimes glossed over in these transitions.
















































Let's personalize your content