Due diligence is ever more critical as the battle for cloud sovereignty intensifies
CIO
DECEMBER 21, 2022
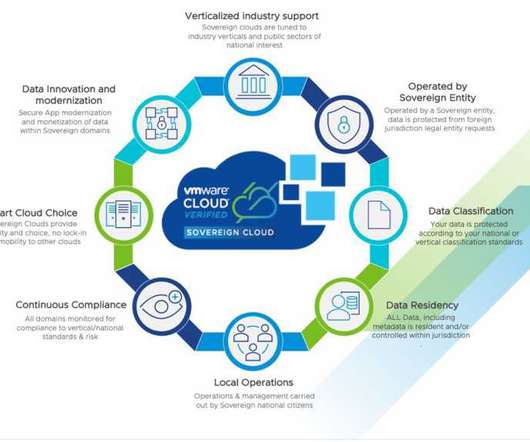
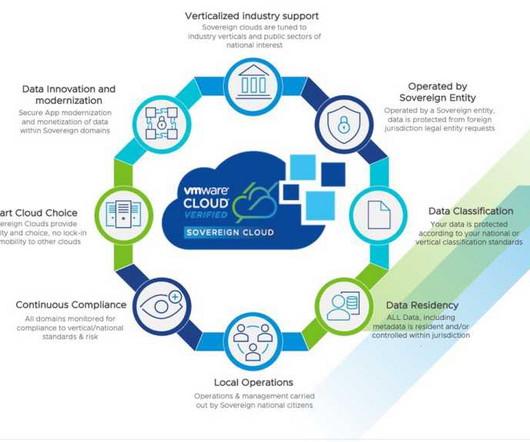
These initiatives reinforce the growing potential of sovereign cloud services in a world increasingly dominated by questions of cloud choice and control, and complex compliance requirements. For example, they all also require jurisdictional control, – which cannot be assumed to be met with a data resident cloud, particularly for U.S.


















































Let's personalize your content