What’s next for network operations
CIO
MARCH 20, 2023
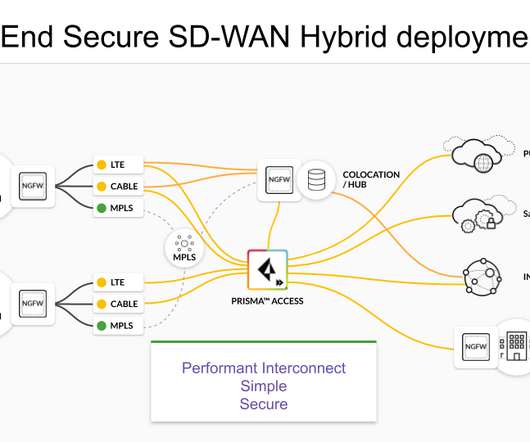
Traditional enterprise wide area networks, or WANs were designed primarily to connect remote branch offices directly to the data center. They rely on centralized security performed by backhauling traffic through the corporate data center, which impairs application performance and makes them expensive and inefficient.



















































Let's personalize your content