IT’s role in moving the organisation towards a circular economy
CIO
MARCH 6, 2024
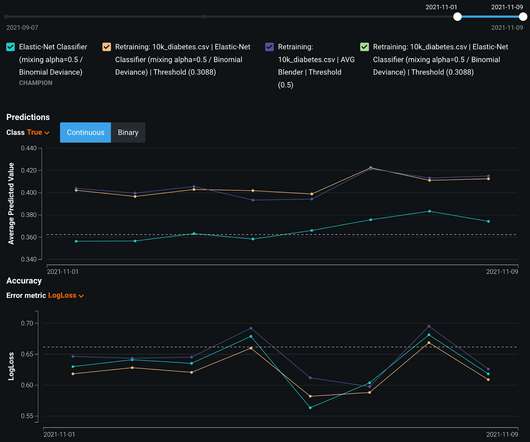
A circular economy strategy must include visibility across the entire product lifecycle, from product lifecycle management to supply chain sourcing and beyond. While HP’s Device Recovery Service ensures end-of-use devices are securely collected, sanitised, and restored or responsibly recycled.


























Let's personalize your content