Start your zero-trust journey with ZTNA over VPN
CIO
JANUARY 19, 2024
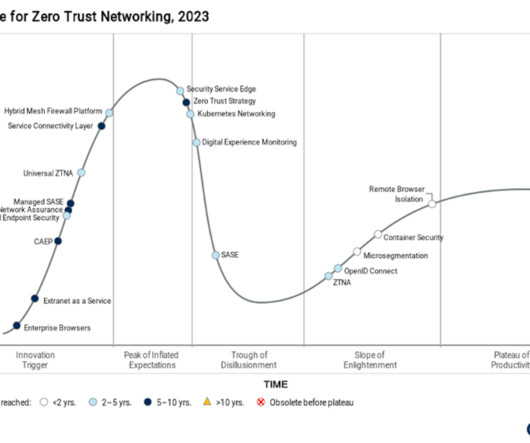
Consequently, the first zero-trust solution many IT teams deploy on their zero-trust journey is zero-trust network access (ZTNA). ZTNA improves security by performing user identity and device posture checks before granting the user or device explicit access to any application.






















































Let's personalize your content