How to minimize remote access cyber security threats in 2024
CIO
JANUARY 22, 2024
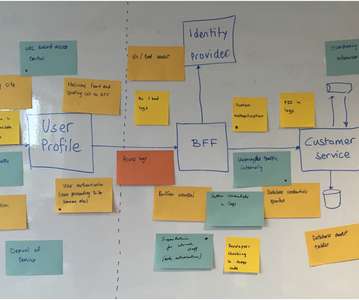
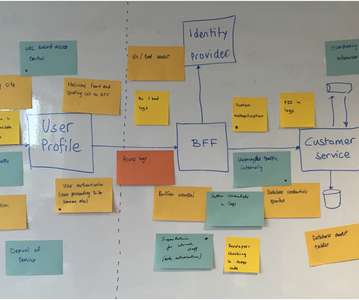
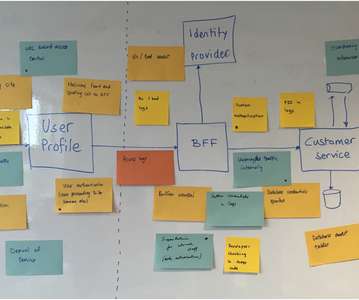
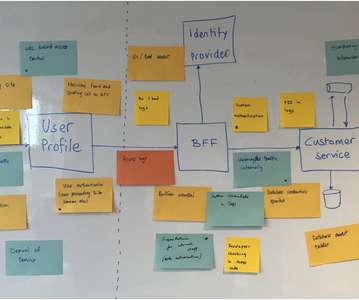
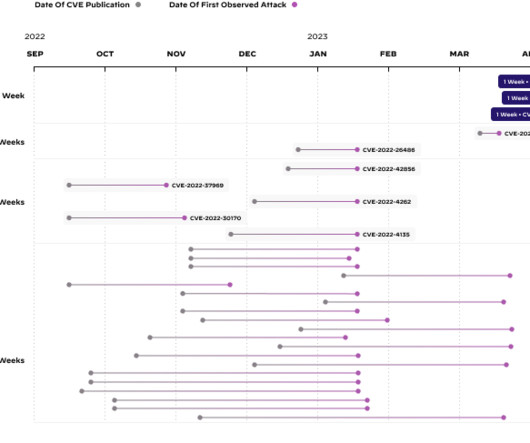
Organizations have shifted to remote desktop work environments at an increasing speed since then – simultaneously expanding their attack surface and exposing themselves to greater cybersecurity threats. Given that threat actors exploit critical vulnerabilities within mere hours of publication, this poses a serious security risk for companies.















































Let's personalize your content