More connected, less secure: Addressing IoT and OT threats to the enterprise
CIO
NOVEMBER 14, 2023
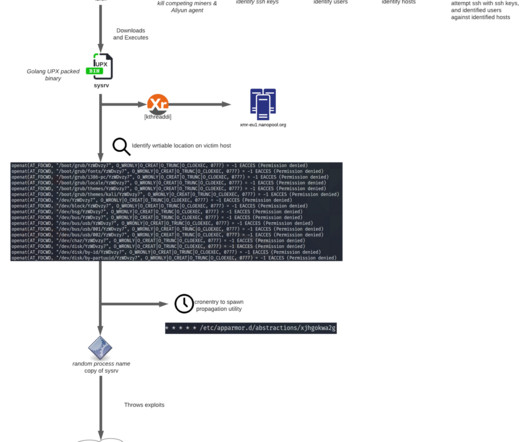
These issues are akin to leaving the front door to your digital infrastructure unlocked. Malware is the top threat to IoT/OT With so many vulnerabilities plaguing IoT devices, these devices are attractive and relatively easy entry points into corporate networks for attackers. of the total number of attempted IoT malware attacks.



















































Let's personalize your content