CISA’s Malware Analysis Platform could Foster Better Threat Intel
Ooda Loop
APRIL 15, 2024
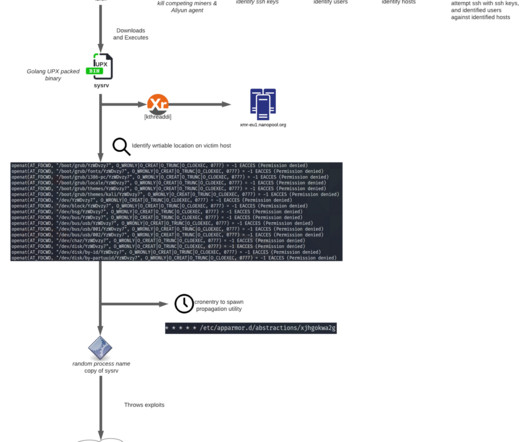
The US Cybersecurity and Infrastructure Security Agency (CISA) has given organizations a new resource for analyzing suspicious and potentially malicious files, URLs, and IP addresses by making its Malware Next-Gen Analysis platform available to everyone earlier this week.



















































Let's personalize your content