Build.security raises $6M for its authorization policy management platform
TechCrunch
NOVEMBER 18, 2020
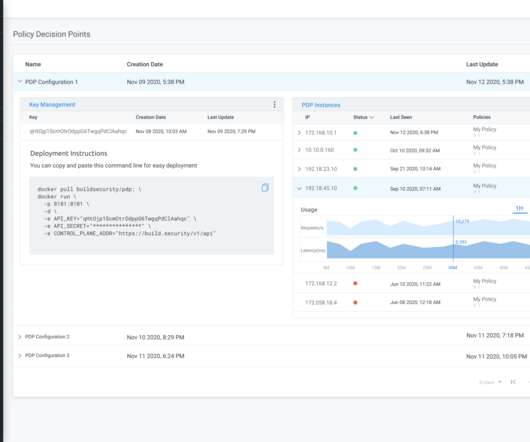
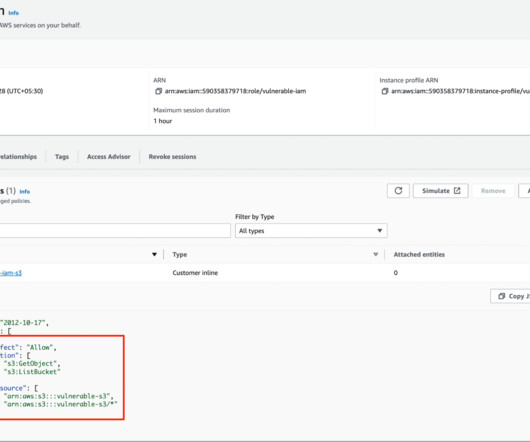
Build.security, a Tel Aviv and Sunnyvale-based startup that aims to make it easier for developers to bake authorization policy management right into their applications, today announced a $6 million seed funding round led by cybersecurity-centric firm YL Ventures. Image Credits: build.security. It’s not an easy task.”




















































Let's personalize your content