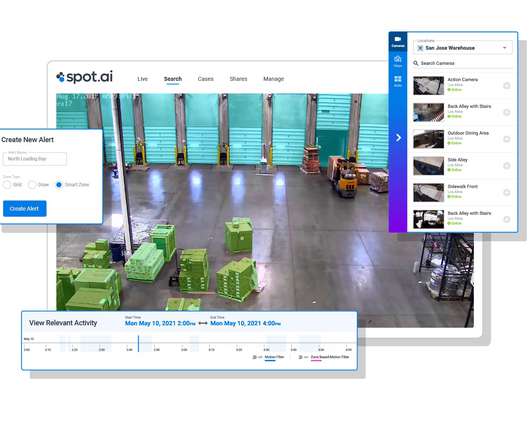
Secure data-first modernization? Leverage a trusted ecosystem of partners
CIO
MARCH 8, 2023
This can help IT teams map the right set of services to unique workflows and to ensure that data is securely managed and accessible regardless of location. Yet there’s no singular, one-size-fits-all framework for secure data storage and management. Upgrading IT and data security to reduce corporate risk was the No.




















































Let's personalize your content