Don’t gamble with your identity verification practices
CIO
OCTOBER 16, 2023
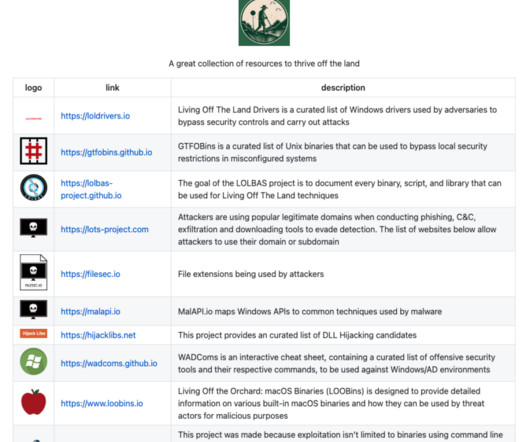
Earlier this year, I wrote about the importance of organizations reviewing their password management strategies. According to a Reuters report, these ransomware bandits also breached the systems of several other companies operating in manufacturing, retail, and technology. IBM Security pegged that same number higher, to 95%.



















































Let's personalize your content