Cybersecurity for enterprise: 10 essential PAM considerations for modern hybrid enterprises
CIO
DECEMBER 7, 2023
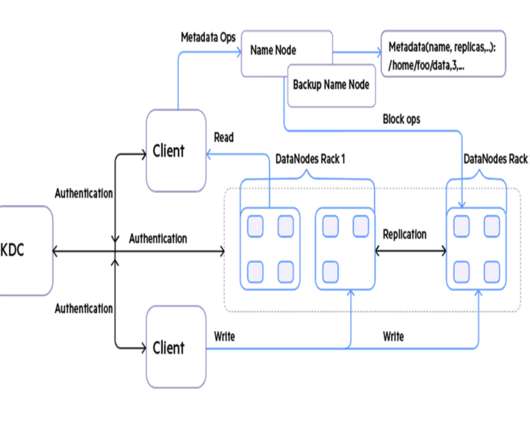
Supporting enterprise security during a cloud migration can be rife with pitfalls that can derail the initiative and ruin the customer experience. She joined the company in the middle of a corporate cloud transformation initiative and inherited a new Privileged Access Management (PAM) solution as part of an enterprise cybersecurity overhaul.












































Let's personalize your content