How Lacework Composite Alerts caught a Windows incident: A detailed walkthrough
Lacework
APRIL 16, 2024
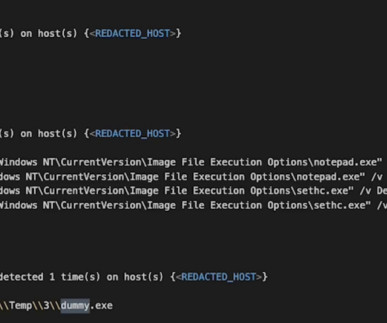
Here is what a Composite Alert looks like in a Windows environment: In this case, the customer was running an automated testing tool to simulate a wide range of attacks on their Windows environment, essentially throwing everything it could at the system to find weaknesses. Why is Windows a target?












































Let's personalize your content