Why endpoint security will be a renewed priority for businesses of all sizes in 2023
CIO
NOVEMBER 23, 2022
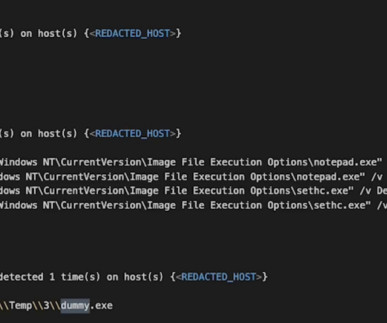
Ransomware often starts from something as humble as someone in the organisation downloading the wrong file from an email. Misconfigurations and unpatched systems – cyber criminals can purchase tools from dark Web marketplaces that will scan IT networks and devices for poor configurations and unpatched systems that they can exploit.




















































Let's personalize your content