EventStorming; Core concepts, glossary and legend
Xebia
JULY 16, 2020
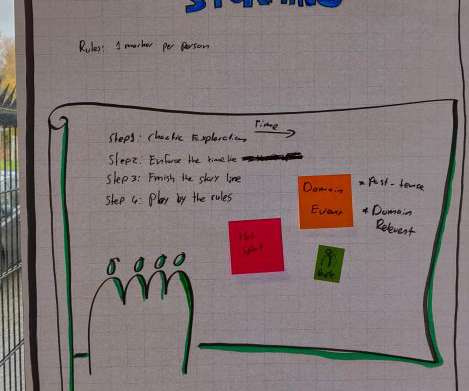
Recently on Twitter Chris Richardson asked if anyone has created a consistent and comprehensive glossary for EventStorming core concepts. I replied saying that #EventStorming is fuzzy by design. There are standard core concepts, and depending on the context, we use different words for the post-its. Because with that fuzziness, you get more insights.





































Let's personalize your content