Generative AI: Balancing security with innovation
CIO
SEPTEMBER 7, 2023
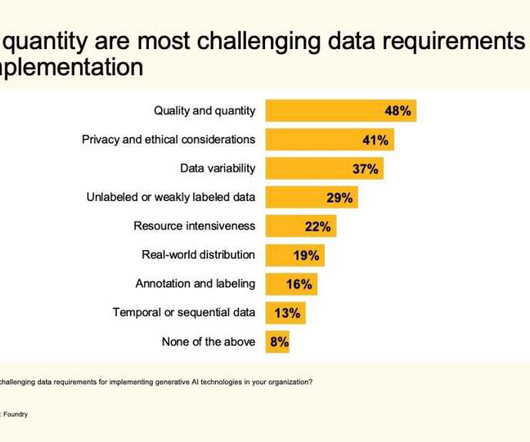
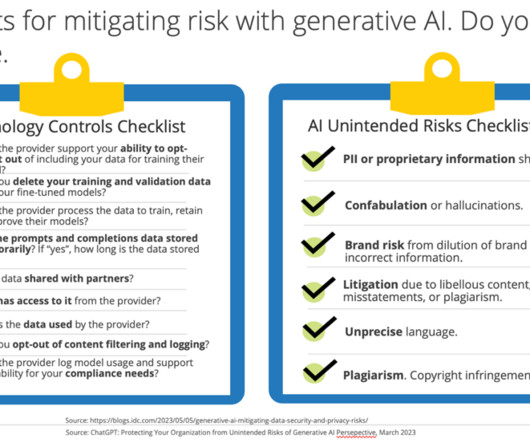
Slowing the progression of AI may be impossible, but approaching AI in a thoughtful, intentional, and security-focused manner is imperative for fintech companies to nullify potential threats and maintain customer trust while still taking advantage of its power.




















































Let's personalize your content