Securing 5G for 2023 and beyond
CIO
FEBRUARY 24, 2023
By Anand Oswal, Senior Vice President and GM at cyber security leader Palo Alto Networks While mobile technology has been around for decades, the current generation, 5G, is increasingly being recognized for the exciting new benefits it brings to enterprises, SMBs, and public sector organizations. Radio rogues.















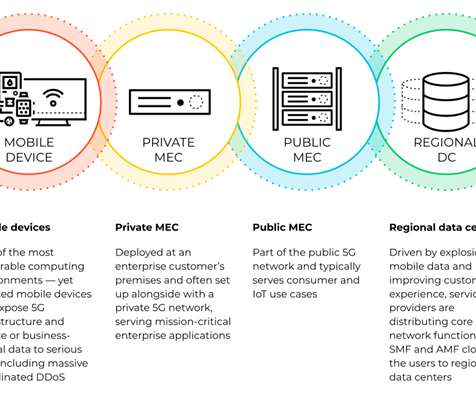
























Let's personalize your content