Halcyon lands large investment to defend against ransomware
TechCrunch
APRIL 20, 2023
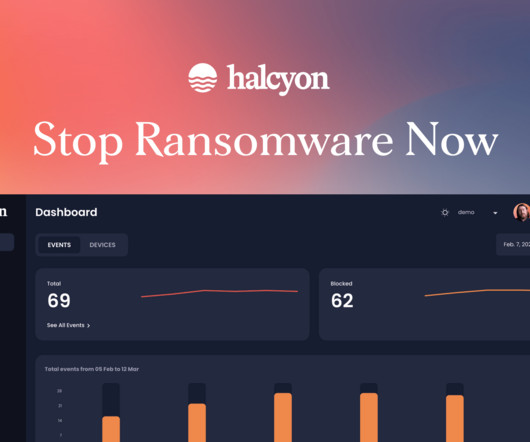
Seventy-eight percent of companies responding to a recent survey said that they plan to increase their investments in cybersecurity in the next 12 months. “With the growth of ransomware operations and the economy that supports them, gaining access to credentials and systems is easier and cheaper than ever before,” Miller said.


































Let's personalize your content