Cathay Pacific to take cloud journey to new heights
CIO
JANUARY 8, 2024
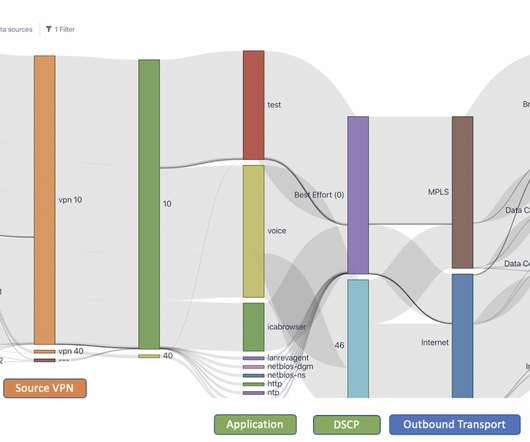
Cloud optimization is the new initiative in 2024,” says Rajeev Nair, general manager of IT infrastructure and security at Cathay, a major airliner and cargo carrier in the Asia-Pacific region, with headquarters in Hong Kong. It will replace the standard MPLS network, he adds. It will replace the standard MPLS network, he adds.


















































Let's personalize your content