Automation for all—managing and scaling networks has never been easier
CIO
APRIL 27, 2023
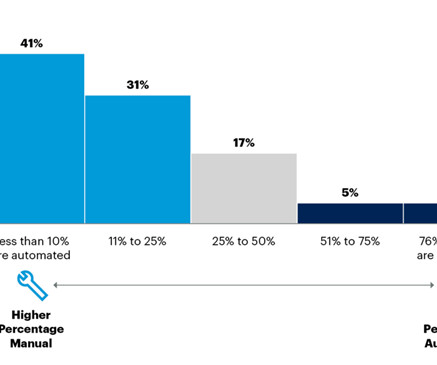
At this time of dynamic business and market changes, uncertainty, and quickly evolving consumption models for IT infrastructure, every IT executive understands the benefits and necessity of network agility. Agile networks can respond quickly to changes in the market, customer demands, employee requirements, and technology advances.
















































Let's personalize your content