Tenable Bolsters Its Cloud Security Arsenal with Malware Detection
Tenable
MAY 1, 2024
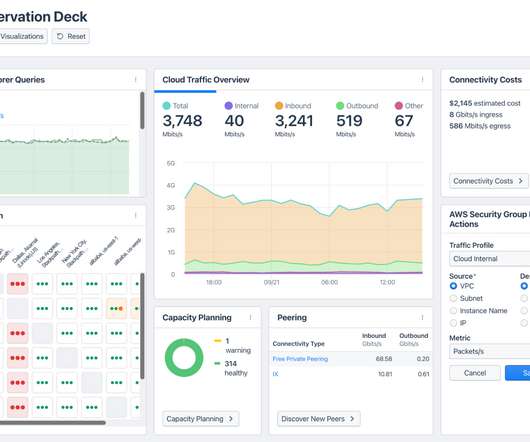
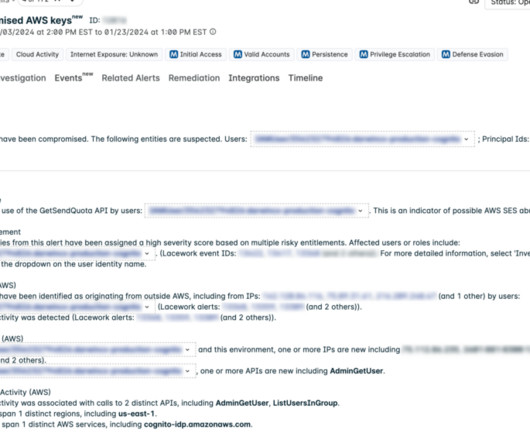
Tenable Cloud Security is enhancing its capabilities with malware detection. Even though cloud adoption has become mainstream, many threats and attack tactics still rely on malware payloads. Tenable Cloud Security can now find malware in many different cloud workloads. The addition of malware detection enhances this approach.



















































Let's personalize your content