TechCrunch+ roundup: Generative AI for proptech, cloud vendor shopping, cybersecurity fairy tales
TechCrunch
FEBRUARY 7, 2023
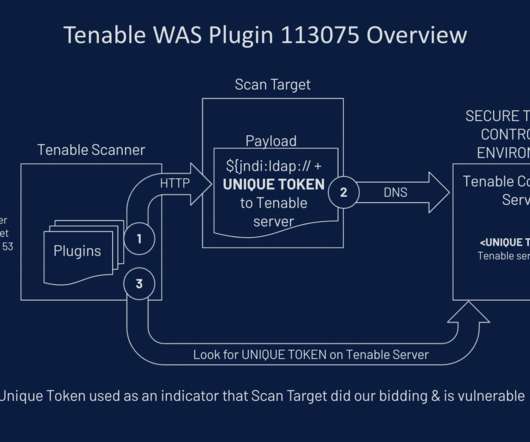
Cybersecurity teams, beware: The defender’s dilemma is a lie Image Credits: A. Martin UW Photography (opens in a new window) / Getty Images The Defender’s Dilemma is one of cybersecurity’s touchstones: “Defenders have to be right every time. ” It may sound authentic, but David J. .”
































Let's personalize your content