How to run data on Kubernetes: 6 starting principles
TechCrunch
NOVEMBER 25, 2022
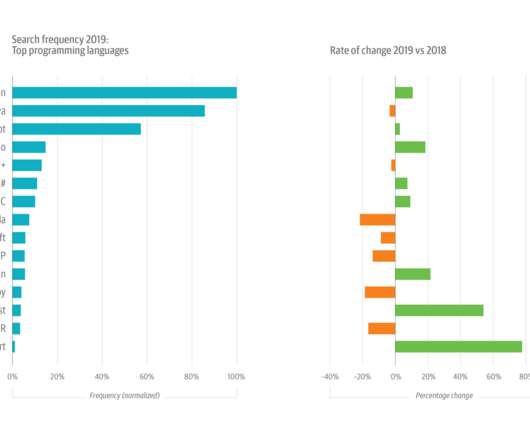
Kubernetes is fast becoming an industry standard, with up to 94% of organizations deploying their services and applications on the container orchestration platform, per a survey. One of the key reasons companies deploy on Kubernetes is standardization, which lets advanced users see productivity gains of up to two times.

















































Let's personalize your content