Cybersecurity Snapshot: CISA Shines Light on Cloud Security and on Hybrid IAM Systems’ Integration
Tenable
MARCH 15, 2024
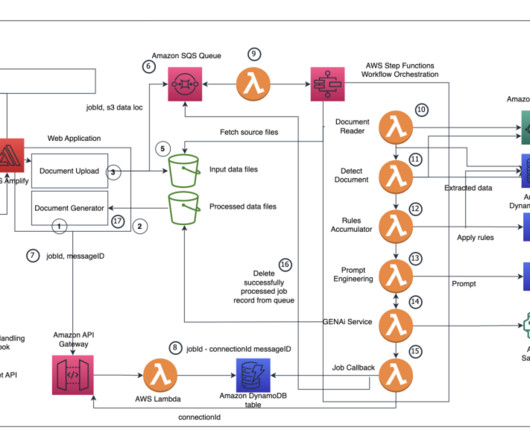
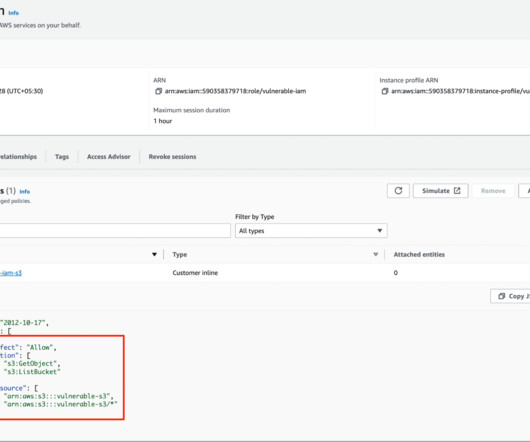
Check out CISA’s latest best practices for protecting cloud environments, and for securely integrating on-prem and cloud IAM systems. 1 - Tips for integrating on-prem and cloud IAM systems Ah, the joys of hybrid environments! Plus, catch up on the ongoing Midnight Blizzard attack against Microsoft. And much more!



















































Let's personalize your content