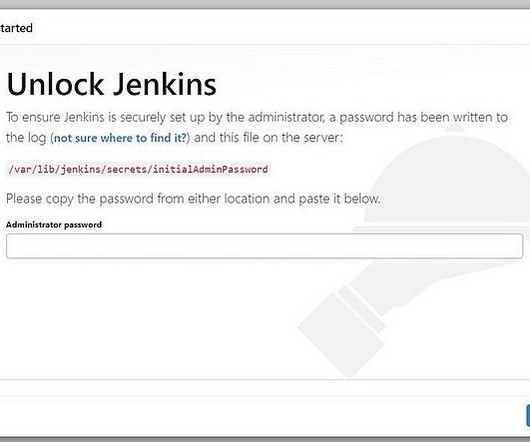
CVE-2023-48788: Critical Fortinet FortiClientEMS SQL Injection Vulnerability
Tenable
MARCH 14, 2024
Critical At the time this blog was published, Fortinet’s advisory assigned a CVSSv3 score of 9.3 This blog will be updated to reflect the correct CVSSv3 score if the advisory or NVD record are updated. At the time this blog was published, Fortinet’s advisory did not include any messaging about known exploitation of this vulnerability.































Let's personalize your content