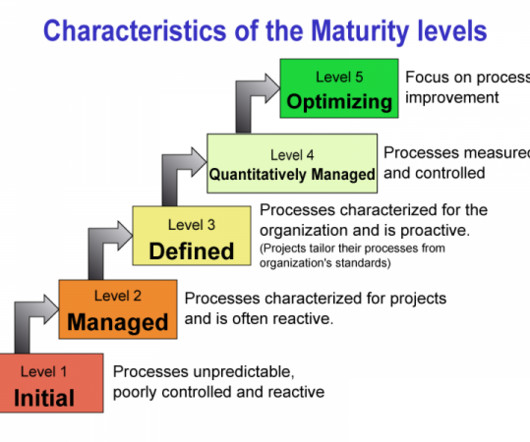
How to make coaching work for your sales team
TechCrunch
SEPTEMBER 30, 2022
The advent of SaaS and cloud-based software services has all but obliterated the traditional sales model, but not many organizations are actually helping their sales teams adapt to this new world order. Every sales team is composed of vastly different individuals who possess distinctive soft skills, behaviors and mindsets.














































Let's personalize your content