Zededa lands a cash infusion to expand its edge device management software
TechCrunch
JULY 21, 2022
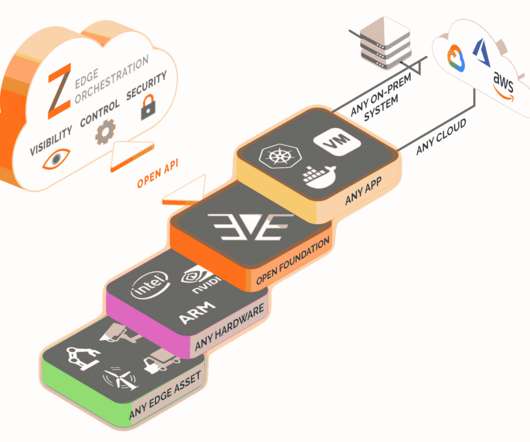
The company raised $26 million in Series B funding, Zededa today announced, contributed by a range of investors including Coast Range Capital, Lux Capital, Energize Ventures, Almaz Capital, Porsche Ventures, Chevron Technology Ventures, Juniper Networks, Rockwell Automation, Samsung Next and EDF North America Ventures. Image Credits: Zededa.













































Let's personalize your content