The power players of retail transformation: IoT, 5G, and AI/ML on Microsoft Cloud
CIO
APRIL 19, 2023
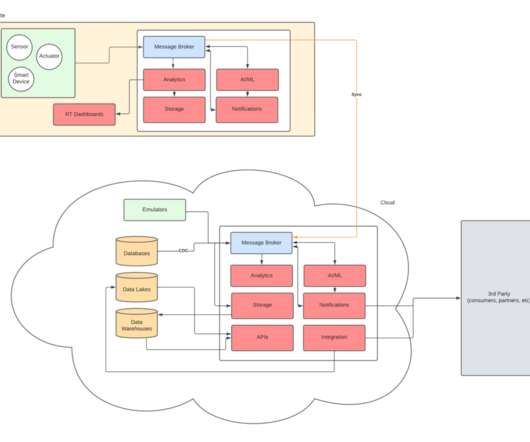
Thanks to cloud, Internet of Things (IoT), and 5G technologies, every link in the retail supply chain is becoming more tightly integrated. Transformation using these technologies is not just about finding ways to reduce energy consumption now,” says Binu Jacob, Head of IoT, Microsoft Business Unit, Tata Consultancy Services (TCS). “The


















































Let's personalize your content