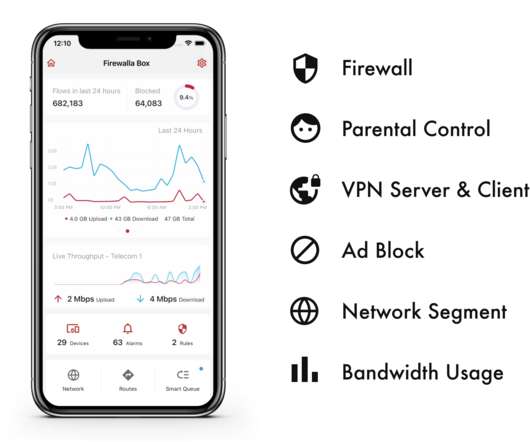
Primer: What DDoS attacks could mean for IoT
The Parallax
JUNE 13, 2018
And although organizations can do certain things to mitigate the impact of an attack, our seemingly ever-increasing usage of Internet-connected devices is likely only inviting more DDoS trouble. DDoS attacks have been around since the Stone Age of the Internet: The first recorded denial-of-service attack dates back to 1974.


































Let's personalize your content