Document Classification With Machine Learning: Computer Vision, OCR, NLP, and Other Techniques
Altexsoft
NOVEMBER 17, 2021
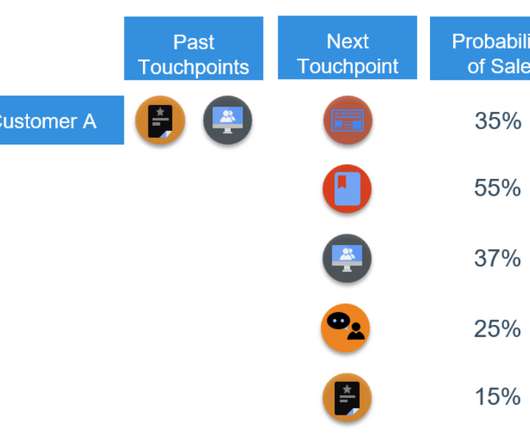
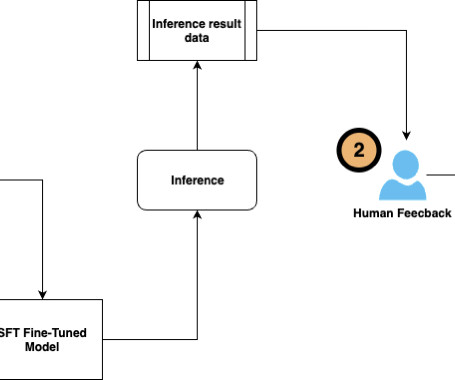
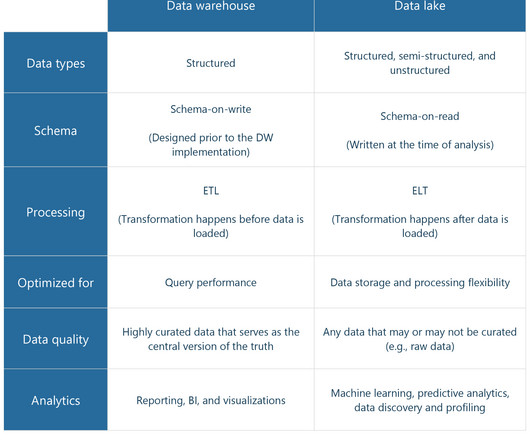
So businesses employ machine learning (ML) and Artificial Intelligence (AI) technologies for classification tasks. Namely, we’ll look at how rule-based systems and machine learning models work in this context. An NLP-based system can be implemented for a ticket routing task in this case.











































Let's personalize your content