Thoughts on organizing architecture
Xebia
AUGUST 3, 2021
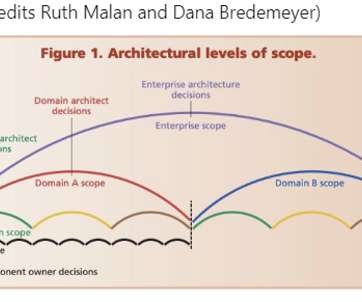
Should the team not be able to make all of these architectural decisions by themselves? Gone are the days of making well-thought documents who are reviewed and tested by colleagues in the organization. Organizing architecture guided by two perspectives. First-of-all, architectural scopes are not to be seen as static elements.















































Let's personalize your content