Generative AI: Balancing security with innovation
CIO
SEPTEMBER 7, 2023
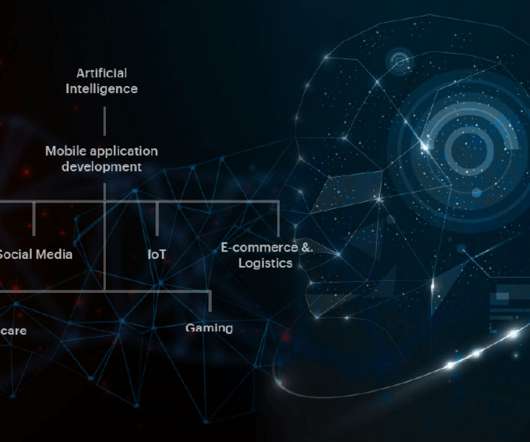
The speed at which artificial intelligence (AI)—and particularly generative AI (GenAI)—is upending everyday life and entire industries is staggering. Whether it’s deep fakes or simply more sophisticated phishing attempts, AI is making it easier to steal identities and ramping up the need for more accurate, faster authentication.





















































Let's personalize your content