TechCrunch+ roundup: Technical due diligence, web3’s promise, how to hire well
TechCrunch
OCTOBER 25, 2022
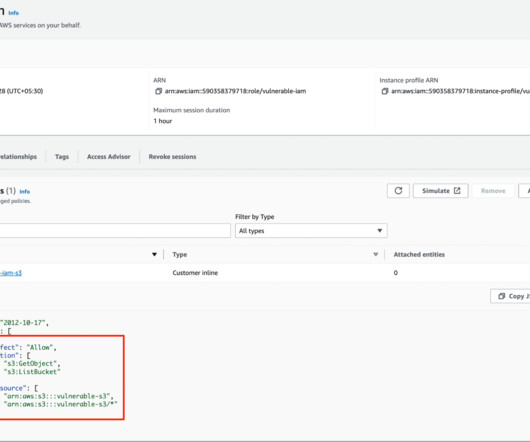
cloud servers.” Then again, I’m not a developer, so I didn’t truly appreciate the value of mobile gaming, GPS and cloud storage until they’d achieved product-market fit and were integrated into my smartphone. .” 8 questions to answer before your startup faces technical due diligence.




















































Let's personalize your content